What Is Third Party Fraud?
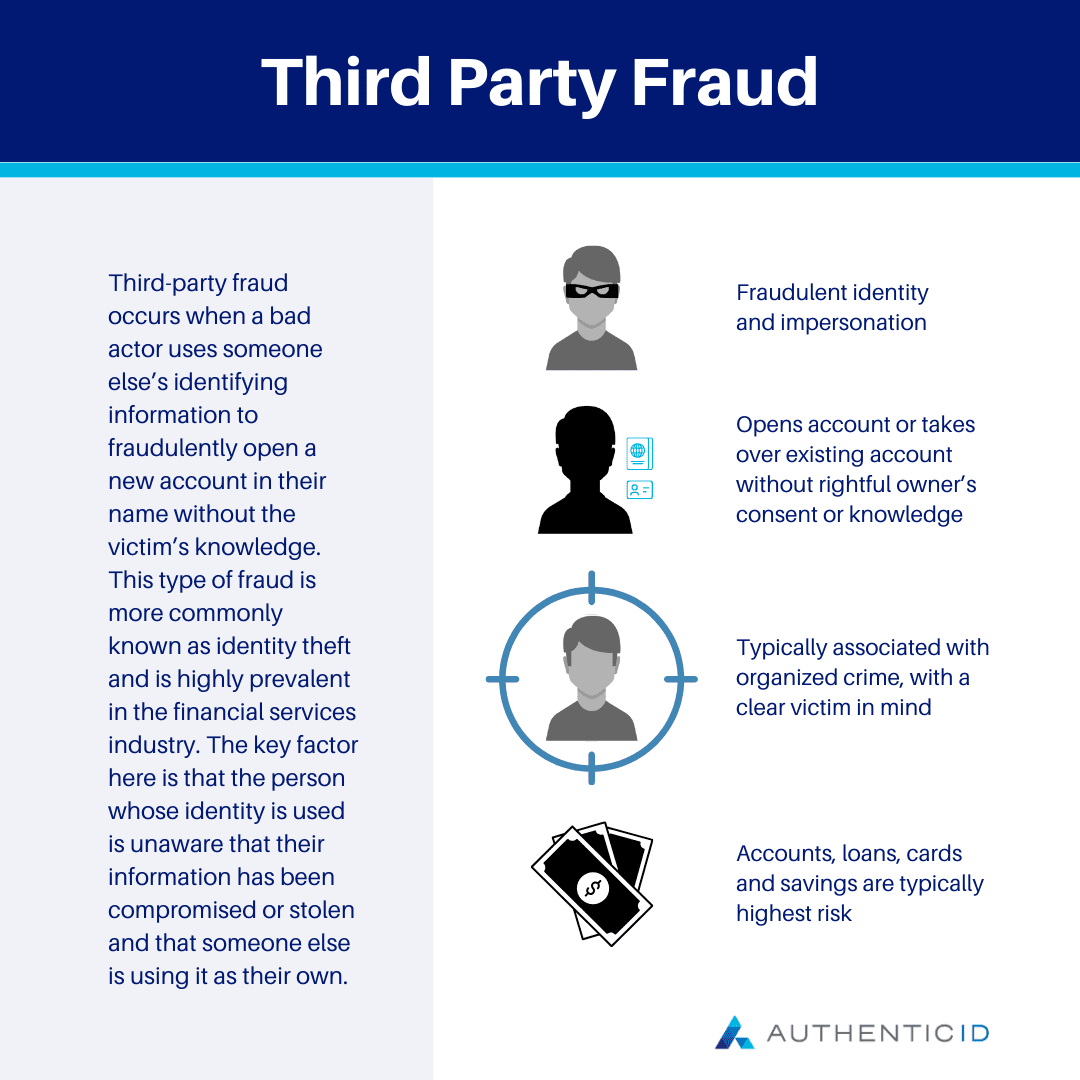
Third-party fraud occurs when a bad actor uses someone else’s identifying information to fraudulently open a new account in their name without the victim’s knowledge. This type of fraud is more commonly known as identity theft and is highly prevalent in the financial services industry.
Fraudsters may use a victim’s identity to secure credit or loan products with no intention of making any repayments. The victim’s credit may suffer if they do not recognize the fraud in time, and the financial institution will have to categorize it as a loss. Thus, third-party fraud can generally go on until the victim has noticed a hit to their credit score or finds an unrecognized account on their credit report.
The key factor here is that the person whose identity is used is unaware that their information has been compromised or stolen and that someone else is using it as their own. Unlike some of the other types of fraud, which we will now review, this is not a scheme they are involved in, and there is a clear victim of the crime.
Third-Party Fraud vs. Second-Party Fraud
There is a key difference between third-party fraud and second-party fraud. Again, with third-party fraud, the person whose information is being used is a victim and does not give consent.
However, in second-party fraud, a person agrees to let another individual use their name or identity to engage in other criminal behaviors. This is common in money laundering schemes, where someone gives their bank account access to a criminal so they can transfer money around and “wash” it in hopes of shielding their illicit activities.
Third-Party Fraud vs. First-Party Fraud
Another important distinction is between third-party and first-party fraud. In this case, a person will purposefully misrepresent themselves to deceive another person or organization for financial gain.
This is commonly seen in applications for financial services like loans, credit cards, or mortgages where a person overstates their income, employment, or credit score to secure the service.
How Does Third-Party Fraud Happen?
Fraudsters can get their hands on exposed personal information in a variety of ways. Unfortunately, there’s not just one method they use; otherwise, it would be much easier to track and prevent.
Here are some of the means that opportunists can use to access compromised identity information and engage in third-party fraud:
- Malicious insiders: The fraudster may work with an employee or staff member on the inside who has access to customer records to misuse their privileges and expose user data
- Phishing attacks: The use of phishing emails or messages aim to get individuals to enter their login credentials, financial data, or other details under the guise that they’re interacting with a legitimate representative of an organization or financial institution they recognize
- Social engineering: The fraudster can use tactics to manipulate individuals into compromising or disclosing their own information, similar to phishing
- Data breaches: Fraudsters may access or purchase compromised identity information on the dark web, which was exposed during large-scale data breaches of enterprises or large organizations
- Malware attacks: Attackers may infect an organization’s systems with spyware, remote access trojans (RATs), or other methods to capture user information
Once the fraudsters have enough personal information on a victim, they can use their identity to open up new accounts and engage in fraudulent activities.
Consequences of Third Party Fraud
Third-party fraud impacts both the individual whose identity was stolen as well as the organizations or institutions where the victim’s identity was used to open up an account on false pretenses.
As such, the consequences of this type of fraud can be widespread, with ripple effects that extend far beyond the initial incidents. This includes:
Financial Loss
Possibly the most notable consequence of third-party fraud is financial loss, both for the individual victim and the institution where the fraudster opened up an illegitimate account. The victim may be able to recover financial damages from the financial institution. However, the business may be on the hook for any unauthorized payments or bad debt, which they may have to write off as a loss.
Legal Ramifications
If customer information is exposed during a data breach or attack on an organization and the data is then used to facilitate third-party fraud, the organization may face legal and regulatory consequences for failing to adequately prevent or detect the incident. These consequences might include fines, penalties, or other regulatory sanctions.
Reputation Damage
Overall, an institution involved in third-party fraud can suffer reputational damage, even if they themselves fall victim to the fraudsters’ actions. The victim whose identity was stolen and used to open up an account at a certain financial institution may forever associate the organization with fraud, loss, and damage, even if they didn’t play a knowing role in the crime.
Preventing Third-Party Fraud
As we mentioned above, a person’s identity information can be exposed to criminals in various ways, meaning individuals and organizations must take a comprehensive approach to preventing third-party fraud.
These are some of the preventative measures that can help safeguard individuals’ information and keep their data from falling into the wrong hands:
- Enable strong authentication mechanisms for user and employee accounts to prevent unauthorized access to their information
- Train employees on the latest phishing techniques and fraudulent tactics to be aware of
- Educate customers on current fraud risks, and provide helpful tips to help them keep their information safe
- Leverage fraud detection tools to identify patterns of behavior that indicate fraudulent behavior is underway