In the case of an account takeover, both individuals and larger organizations face serious threats and consequences regarding their reputation and online security. As fraudsters’ tactics become more advanced and sophisticated, it’s important to know the best fraud detection methods, what the motives are behind account takeovers, and methods of detection.
As the world moves increasingly online–both for professional and personal use–the risk of an account getting hacked and personal or sensitive information being leaked only continues to rise. With potential financial devastation, identity fraud, and compromised sensitive information at stake, everyone who has at least one online account is at risk.
What Is an Account Takeover?
An Account Takeover refers to a type of cyber attack that occurs when a hacker gains access to an online account without authorization. Typically, this is done for malicious purposes and for the personal gain of the perpetrator. The hackers that attempt an Account Takeover are often looking for system vulnerabilities to access a user’s account without their knowledge or permission.
This type of crime has developed into a larger industry, with teams of hackers working together to compile lists of verified account credentials, then sell them on the dark web to other cybercriminals who will utilize them to gain unauthorized access to victims’ accounts.
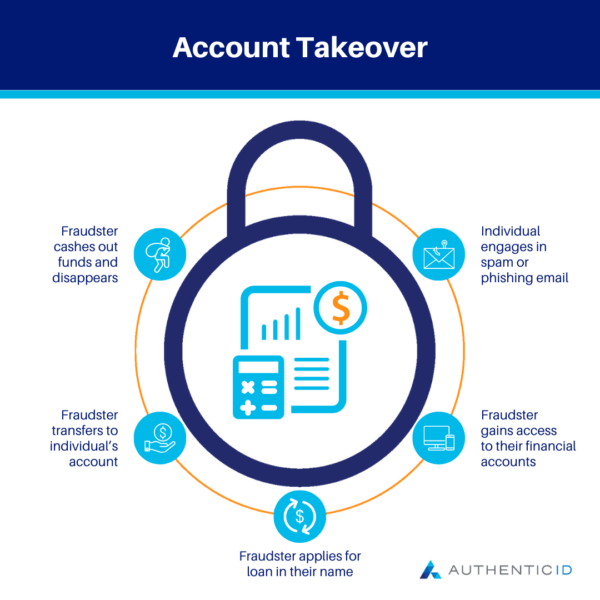
How Does an Account Takeover Happen?
Fraudsters can employ a variety of methods and tactics to carry out an Account Takeover. In the past, criminals may have simply attempted to guess user login credentials to gain unauthorized access to their accounts. However, the advancement of technology and the growing prevalence of data online has allowed them to use more advanced tactics.
Here are some of the most common methods of hackers for an Account Takeover today.
- Social Engineering: attackers try to manipulate or coerce account holders to divulge their login credentials through social interactions
- Phishing: cybercriminals use deceptive emails, messages, or websites to lure account holders to disclose their login credentials
- Credential Stuffing: attackers use automated tools to try out different combinations of compromised usernames and passwords on multiple websites, seeking to take advantage of users who reuse credentials across multiple accounts
- Brute Force Attacks: hackers attempt a large number of combinations of different passwords and usernames until they find one that allows them to access an account
- Malware: cybercriminals will use malicious software to gain access to the user’s device and capture login credentials through keyloggers or password stealers
Common Motives for an Account Takeover
Unfortunately, there are many reasons why a cybercriminal would be motivated to take over an online account.
Some of the main motives behind an Account Takeover include financial gain or to disrupt an organization’s operations. Once they have gained access to the compromised account, the hacker may want to initiate fraudulent transactions or transfers from the user’s account to their own personal bank account.
Additionally, a successful Account Takeover allows the criminal to access the user’s personal data, which they can then sell or utilize for their own advantage through identity theft. They may use this stolen identity to commit further fraudulent activities and crimes, or apply for financial services and products like loans or credit cards.
The hacker may attempt to perpetuate the Account Takeover scam by spamming the compromised account holder’s personal contacts with messages containing malware or phishing attempts. Thus, their scamming and fraudulent activity can continue as they cast out a wider web to more individuals.
Risks of an Account Takeover
There are many consequences to individuals and corporations should they fall victim to an Account Takeover ploy.
- Financial Loss: Probably the most signifcant risk to people who have had their accounts taken over by cybercriminals is financial loss. Accounts with financial institutions are often the targets of Account Takeovers, as you may be able to imagine. With access to your bank account or credit card account, the fraudster could initiative fraudulent payments to themselves or make larger purchases for themselves, leaving you with financial loss.
- Reputational Damage: If an unauthorized user takes over your account and begins to post inappropriate or malicious content, there can be serious reputation damage. Both individuals and corporations could end up dealing with a loss of trust from those in their network, even if it is revealed that the content was posted by a bad actor.
- Identity Theft: An Account Takeover can expose your private personal information to cybercriminals, who may use the data to open up a bank account, apply for loans, and other criminal activities. Identity theft impacts over 50,000 people in the United States each year, so this isn’t a rare occurrence.
Plus, it can be very costly and time-consuming for those impacted to untangle the web of crimes and fraudulent activity that the hackers have entered into using their personal information.
- Privacy Invasion: Aside from the other negative effects of this type of fraud, falling victim to an Account Takeover can be very invasive to the victim. Just as you would feel a sense of unsease and a loss of safety if someone were to break into your home, a similar feeling of vulnerability can be caused when someone “breaks into” your online assets.
Users can help prevent Account Takeovers from occurring through a combination of user education, robust authentication methods, regular password changes, and regular monitoring for suspicious activity.
For this reason, many organizations will employ Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) to enhance account security and mitigate the risk of unauthorized account access.
Additionally, it’s important to stay vigilant and know how to spot an attempted Account Takeover so the severity of the event can be minimized. Here are some warning signs to watch out for to help you detect if you’ve become the target of an Account Takeover:
- Password reset requests: be wary of any notifications for password resets that you did not initiate; it may be a phishing attempt
- Unusual activity: monitor your account regularly for any signs of suspicious or unusual activity like log ins, purchases, etc.
- Unexpected emails/texts: be cautious of opening up any emails or texts that want you to click on a suspicious link or share sensitive information

